View identity providers in the Identity providers grid
The Identity providers - all providers grid shows information for all configured providers in three columns: Display name, Type and Status. Each row has a context menu which you can open by clicking on the context menu icon (...). There is one context menu option available in view mode: Open.
To load the Identity providers - all providers grid, click on the Identity providers menu option in the main ATS Security menu.
Identity provider statuses
Each identity provider can be enabled or disabled. For each enabled provider a button appears in the login dialog, which enables users to login using their external account in the selected provider. The button shows the Display name of the enabled identity provider.
Multiple identity providers of the same type can be enabled simultaneously. In this case all buttons for providers of the same type appear in the same color on the login page.
The exception of this rule is the Windows type of identity provider. There can only be one identity provider of type Windows in ATS Security.
Changes related to identity provider settings, enabling and disabling, also adding and removing providers will be applied only after application restart (restarting the respective application pool on the host).
When the user logs in using an external provider account for the first time a matching user is created in the ATS Security database. The source property of this user is set to the external provider type. This user is used for configuring roles and rights for the registered applications.
View identity provider details in the Identity provider details blade
The Open option from the context menu loads the Identity provider details blade on the right and displays details about the provider such as Type, Display name, status info and other properties depending on the provider type. These details are all read-only when in view mode.
Edit identity providers in the Identity providers grid
Each row in the Identity providers - all providers grid has a context menu which you can open by clicking on the context menu icon (...). The context menu options available in edit mode are:
Open
Delete
Disable (for enabled identity providers)
Enable (for disabled identity providers)
Delete an external identity provider
To delete an identity provider:
Select the Delete option from the provider's context menu.
Click on the Yes button in the confirmation pop-up window.
A success notification appears once the delete operation is successfully completed. The deleted identity provider is no longer visible in the grid.
Deleting a disabled provider is effective immediately. For the deletion of an enabled provider to be effective the ATS Security application (application pool) needs to be restarted on the host machine.
Enable/Disable Identity provider
Only enabled identity providers appear as login option on the login page.
To disable an enabled identity provider:
Select the Disable option from the provider's context menu.
Click on the Yes button in the confirmation pop-up window.
A success notification appears for the successfully updated provider. The status of the provider in the Identity providers - all providers grid is set to disabled. This change will become effective only after application pool restart on the host machine.
To enable a disabled identity provider:
Select the Enable option from the provider's context menu.
Click on the Yes button in the confirmation pop-up window.
A success notification appears for the successfully updated provider. The status of the provider in the Identity providers - all providers grid is set to enabled. This change will become effective only after application pool restart on the host machine.
Edit provider from Identity provider details blade
The Open option from the context menu loads the Identity provider details blade on the right and displays details about the provider such as Type, Display name, status info and other properties depending on the provider type.
Two options, Save and Save and close, are disabled until the contents of the fields are modified.
When clicking the Save option all the entered data is saved and the same blade remains open.
When clicking the Save and close option all the entered data is saved, the blade is closed, and the user is redirected to the parent blade.
In addition, if the form fields in a details blade remain unchanged it is possible to work with the "parent" grid (the users grid). Once modifications are made in the Identify Providers details blade the Identify Providers grid becomes "disabled" and grid interactions are no longer possible until the changes are saved or the details blade is closed.
Navigating to another tab in the blade without explicitly saving any changes made in the previous tab will cause the changes to be lost. Clicking on the X button in the blade header closes the Identify Providers details blade, with any changes which were not saved being lost.
To edit an identity provider:
Make the desired changes in details blade.
The Save and Save and close option becomes enabled.
Click on Save or Save and close.
In case some of the mandatory fields are empty or fields with custom validation have "invalid" values the Save or Save and close action will not be executed.
First fix all invalid form fields and then click Save or Save and close.
A pop-up is displayed indicating that a restart will be required before the changes are applied.
Click the OK button in the pop-up
If the Save option is clicked, all entered data is saved and the Identity provider details blade remains open. If the Save and close option is clicked all entered data is saved, the blade is closed, and the user is redirected to the parent blade.
An appropriate push notification will appear depending on the outcome and the successfully edited user will appear in the top position of the Identity providers - All identity providers grid.
Enable/Disable identity provider
In the details blade for each identity provider there is an Enable check box which is checked for enabled identity providers or blank for disabled providers.
To enable a disabled provider:
Check the Enabled check-box.
Click the Save or Save and close option in the details blade.
Click on the OK button in the confirmation pop-up window.
To disable an enabled provider:
Remove the check from the Enabled check-box.
Click the Save or Save and close option in the details blade.
Click on the OK button in the confirmation pop-up window.
If the Save option is clicked, all entered data is saved and the Identity provider details blade remains open. If the Save and close option is clicked all entered data is saved, the blade is closed, and the user is redirected to the parent blade.
An appropriate push notification will appear depending on the outcome and the successfully edited user will appear in the top position of the Identity providers - All identity providers grid.
Add New Identity Provider
ATS Security supports the following types of external identity providers:
AzureAD
GitHub
SAML
For each provider type different properties need to be specified when adding new identity providers such as: Client Id and Client secret. These values are provided when registering an account for the provider. Each provider provides instructions how to complete the registration and get these properties.
To be able to support multiple identity providers of the same type in ATS Security it is important to specify a unique Return URL when ATS Security is registered as client at the external provider. To generate the unique URL simply append the client id assigned to ATS Security upon registration at the external party to the Return URL.
For example: If the return URL for ATS Security is http://ats-security.test:5000/ and the assigned client ID upon registration of ATS Security at the external party is 08e8f803-8c57-47b6-b618-71db8075d7c9 then the Return URL for ATS security should be: http://ats-security.test:5000/08e8f803-8c57-47b6-b618-71db8075d7c9.
Identity providers are added through the Add provider form blade.
To open the Add provider blade, click on the Add button in the top right corner above the Identity providers - All providers grid. This button is only visible when in "edit" mode i.e. logged in with a user that has the EditProviders right.
To add a new provider from the Add provider blade:
Select Type for the provider.
Provide Display name (mandatory).
Provide other required properties depending on selected type.
By default the Enabled check box is ticked for new providers. Remove the tick if you want to add a disabled identity provider.
By default the Auto Register check-box is unchecked. Check Auto Register check box if you trust the identity provider and this will result with saving all provided user data bypassing self-registration settings and checks.
Click on the Save or Save and close button.
When adding a disabled provider, the Add provider blade is closed and an appropriate push notification will appear depending on the outcome.
When adding an enabled provider, a pop-up confirmation appears informing you that the changes will take effect after application restart. Click Ok in the pop-up. The pop-up closes and also the Add provider blade is closed and an appropriate push notification will appear depending on the outcome.
If the Save option is clicked, all entered data is saved and the Identity provider details blade remains open. If the Save and close option is clicked all entered data is saved, the blade is closed, and the user is redirected to the parent blade.
An appropriate push notification will appear depending on the outcome and the successfully edited user will appear in the top position of the Identity providers - All identity providers grid.
Azure Identity Provider
Login into the Azure portal (portal.azure.com).
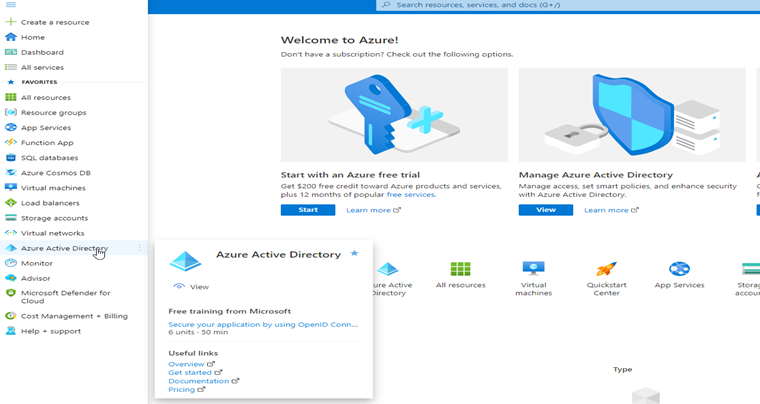
In the main menu navigate to Azure Active Directory.
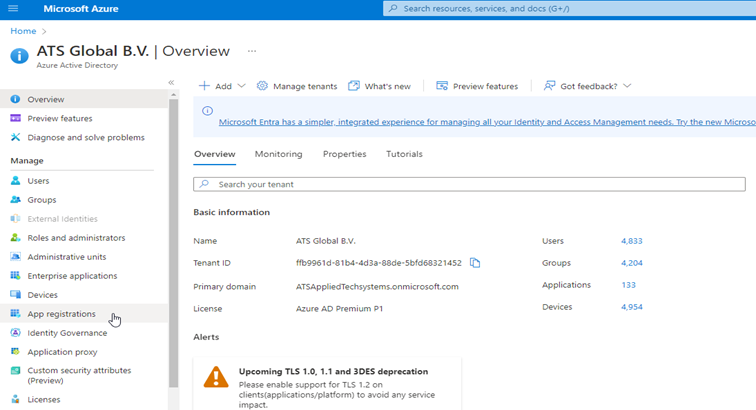
Click App Registrations.
Add a new application registration by clicking on the New registration link (button).
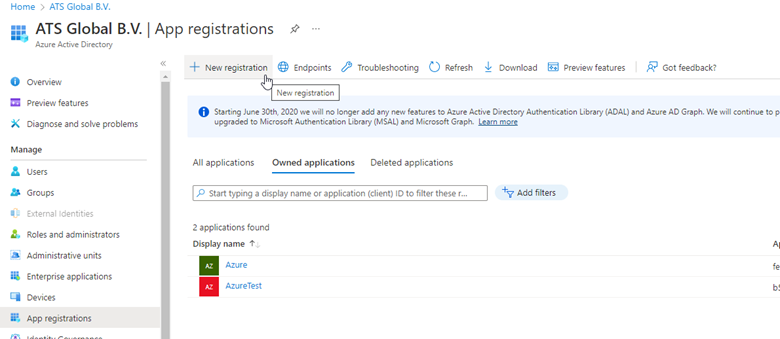
Provide a name for the application.
Set an appropriate option under Supported account types. For example, Accounts in this organizational directory only (ATS Global B.V. only - Single tenant).
Under Redirect URI (optional) select Web and enter the URL of ATS Security.
ATS Security must be configured for HTTPS.
Click Register.
After the application is registered, the application information is displayed. Copy the Application (client) ID value.
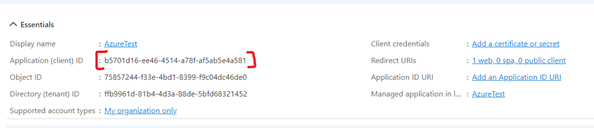
Click the Redirect URIs link.
Click on the URL, which can now be edited, and paste the Application (client) ID so that it is appended to the URL.
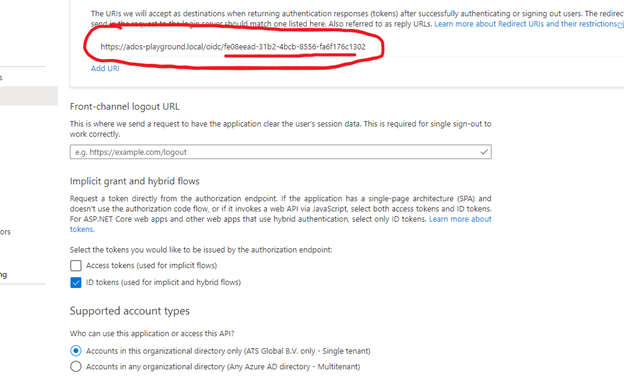
Ensure that the check box for ID tokens (used for implicit and hybrid flows) is checked.
Click Save.
Copy the Application (client) ID and the Directory (tenant) ID, which are required when setting up the Azure external provider in ATS Security Manager.
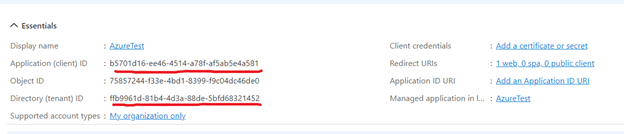
Copy the Value, which is required when Active Directory Groups are used.
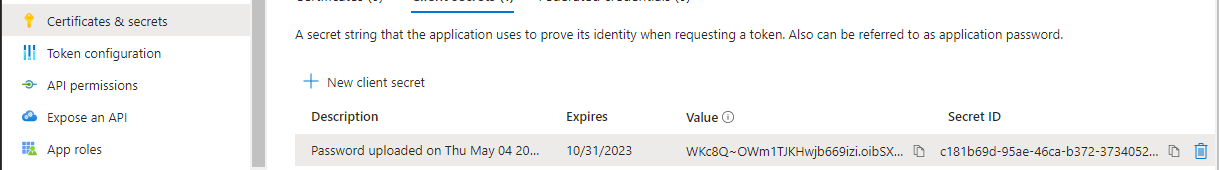
Under Manage, select Token configuration.
Select Add groups claim.
Under Select group types to include in Access, ID and SAML tokens, place a tick in the Security groups check box.
Under Customize token properties by type, select the Group ID token type for ID, Access and SAML.
Select Add.
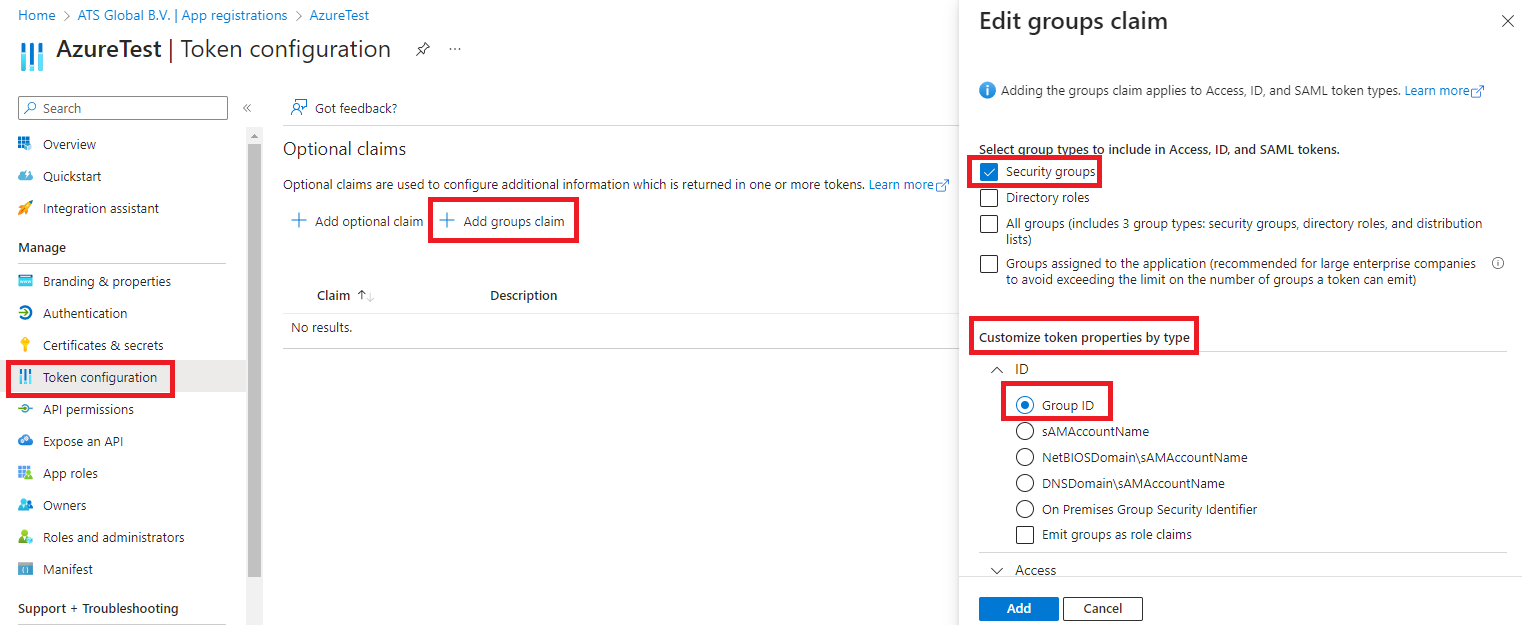
Login to ATS Configuration with a role that has rights to edit identity providers.
Open the Security card followed by the Identity Providers option in the left menu and click on the Add button in the right corner of the grid.
Click on the Select type field and choose the AzureAd type.
Provide a unique display name and enter the Application (client) ID and Directory (tenant) ID.
If Active Directory Groups are being used, copy the Secret ID in to the Client secret field.
Ensure that the provider Is enabled and click Save or Save and close.
Click OK on the pop-up. A success notification will appear indicating that the Identity Provider has been created.
Restart the ATS Security Application.
Logout from the application and load ATS Configuration Manager.
Click on the AzureAd provider button added in this example.
Login with a user from the Azure Active Directory.
The user should be logged in the application
Facebook Identity Provider
Before proceeding with configuring Facebook as an Identity Provider, the user must have a Facebook account.
Go to https://developers.facebook.com/ and click on the Login button in the upper right corner.
Enter the users Facebook credentials and click Log in.
The user is logged in and the Home page is displayed again.
Click on My apps in the upper right corner.
Click on the Create App button.
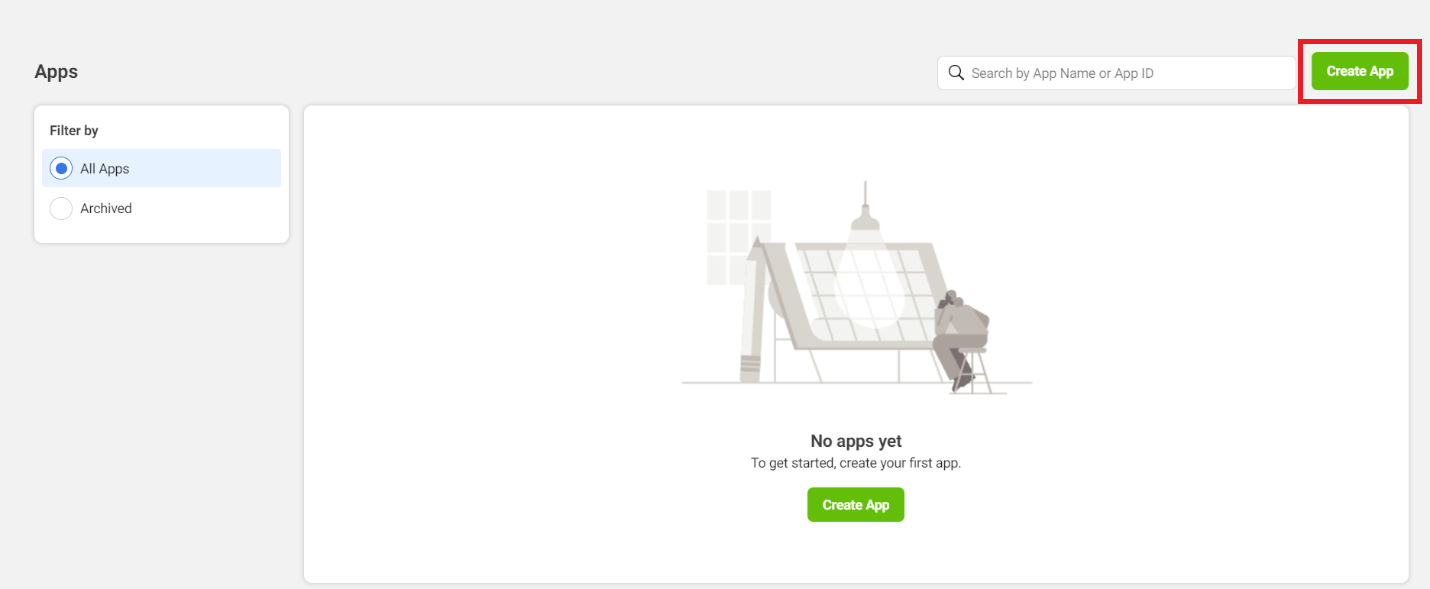
A page is displayed where the user should choose the app type.
Click on None and click Next.
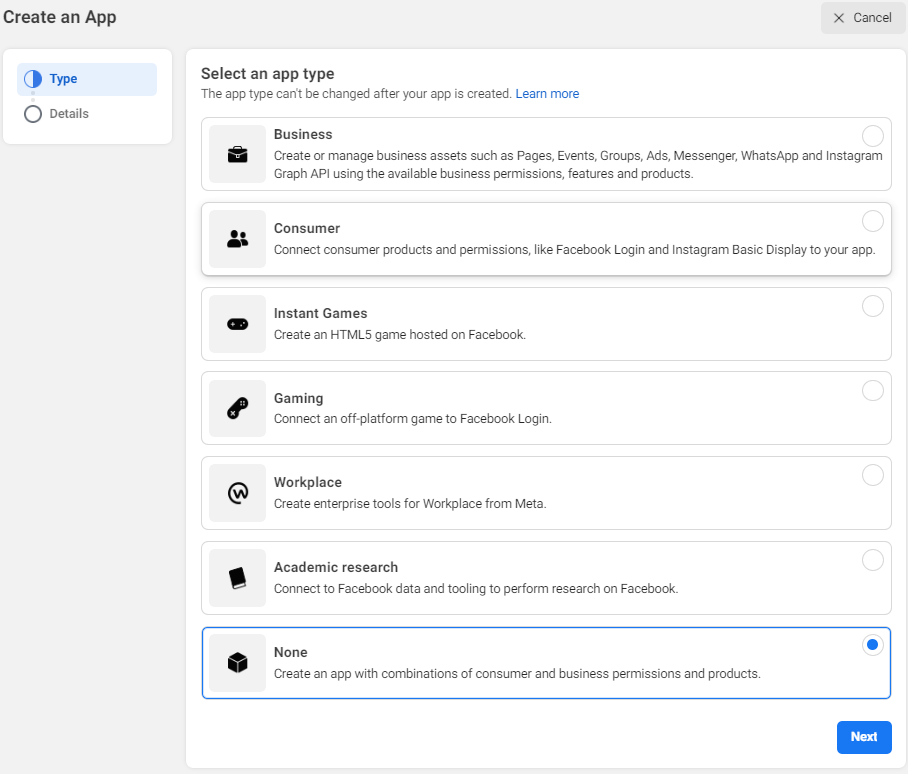
Enter a display name for the app and click the Create app button.
A pop-up will be displayed that requests the facebook password be re-entered. Enter the password and click Submit.
The app is created and the Application ID can be viewed towards the top left of the screen.
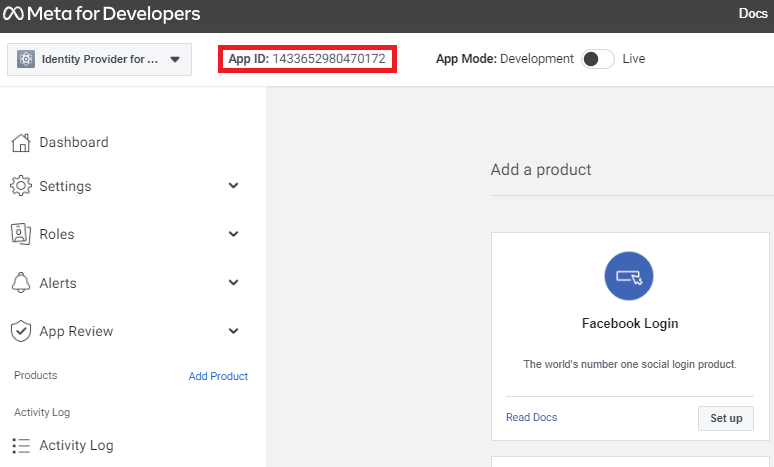
On the Dashboard tab, in the Facebook login square click on the Set up button.
In the left menu, the Facebook login section will be displayed.
Copy the Application Id.
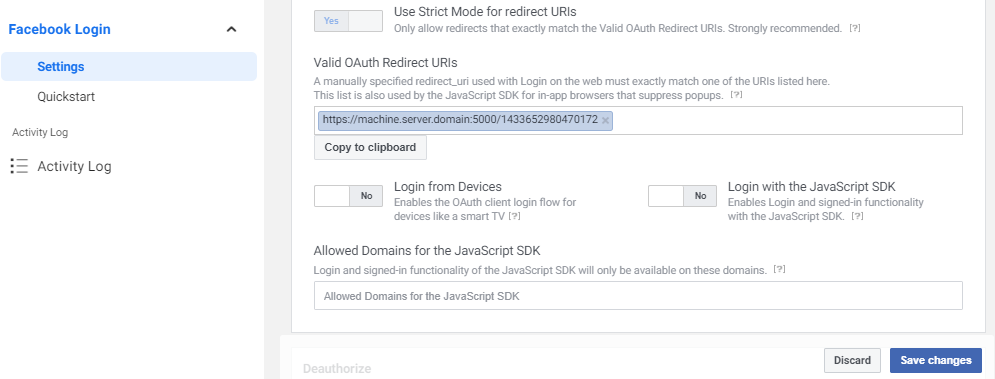
Go to Facebook Login select Settings and in the Valid OAuth Redirect URIs field enter the address where ATS Security Manager is installed appended with the Application Id and click on the Save changes button.
https://machine.server.domain:5000/1433652980470172
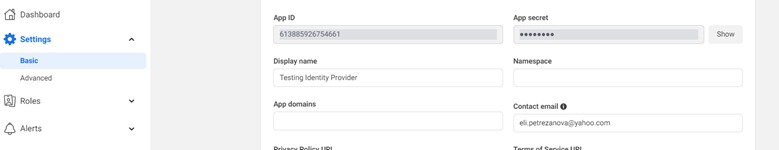
Go to Settings, Basic and make a note of the App Id and App secret.
Load ATS Security and open the Identity providers blade.
Click Add.
Select Facebook in the Type dropdown box.
Enter a Name for the identity provider i.e. Facebook.
Enter the Application ID in the the Client Id field.
Enter the App secret in the Client secret field.
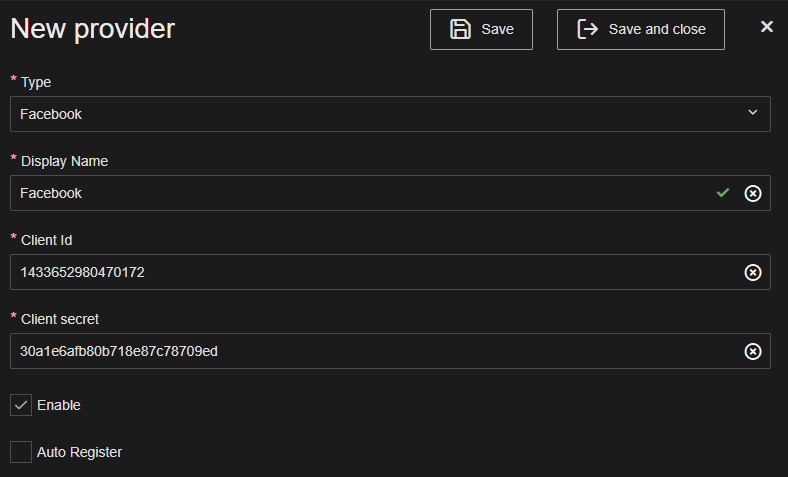
Press Save or Save and close.
The following message will be displayed:
Adding new identity provider of type Facebook. This change will take effect after application restart.
Log out of ATS Security.
Go back to ATS Security and the Facebook logo will be present on the right.
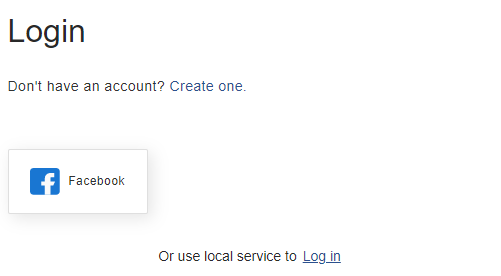
Press the Facebook logo. The Facebook login form is displayed.
Enter the Facebook credentials and click Log in.
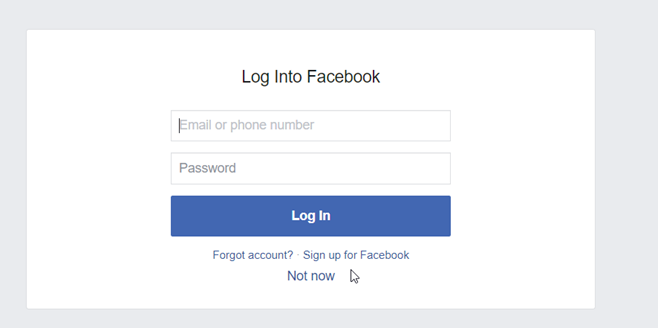
After logging in, the user should be successfully redirected and logged into ATS Security and Configuration Manager.
GitHub Identity Provider
Before proceeding with configuring GitHub as an Identity Provider, the user must have a GitHub account.
Go to https://github.com.
Click on the Sign in button in the upper right corner and log in.
Click on the profile icon in the upper right corner and click on Settings.
The user’s profile is opened.
Scroll down and click on the Developer settings option.
The Developer settings option is displayed.
Click on the GitHub Apps option.
Press the New GitHub App button.
Click on the New GitHub App button.
Enter a display name for the app in the GitHub App name field.
The term GitHub cannot be used in this field.
Enter a placeholder URL in the Homepage URL field.
This field, whilst not used, is required to complete the app registration.
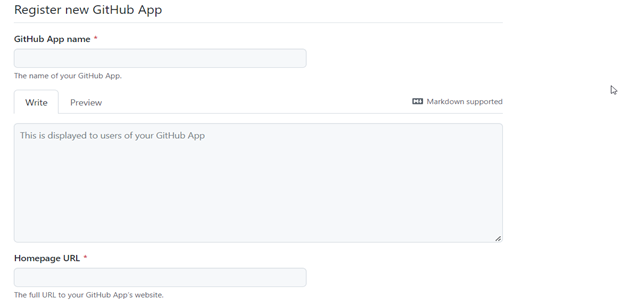
Enter the address of where ATS Security Manager is installed in the Callback URL field.
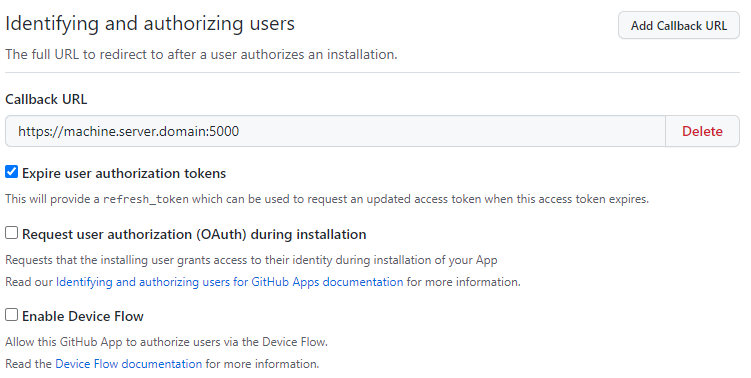
Uncheck the Active check box in the Webhook section.
Set the permissions for Metadata to Read-only in the Repository permissions section.
Set the permissions for Email addresses to Read-only in the User permissions section.
Click on the Create GitHub App button. The following screen will be displayed.
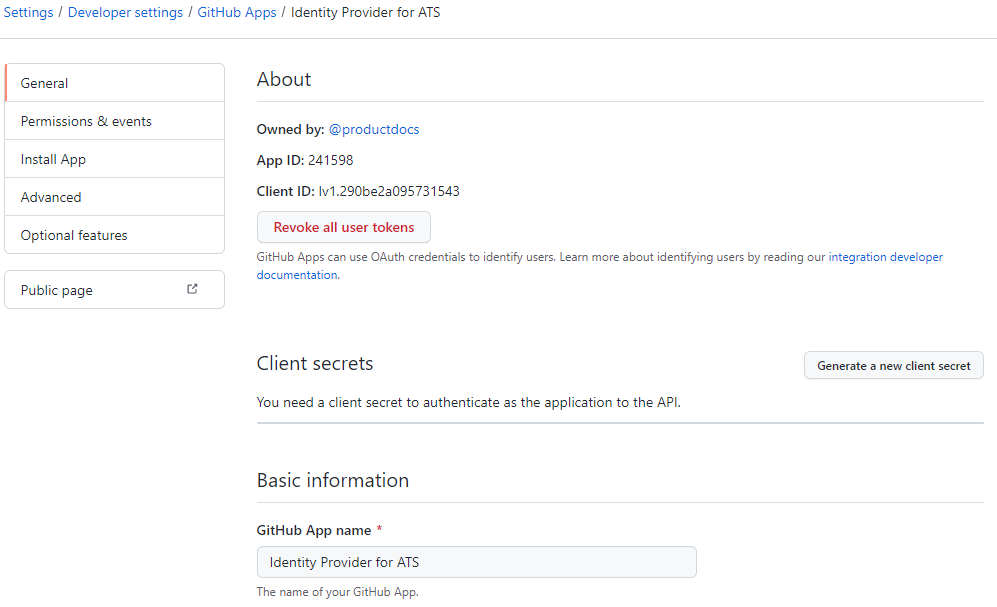
Copy the client ID and append it to the URL in the Callback URL field.
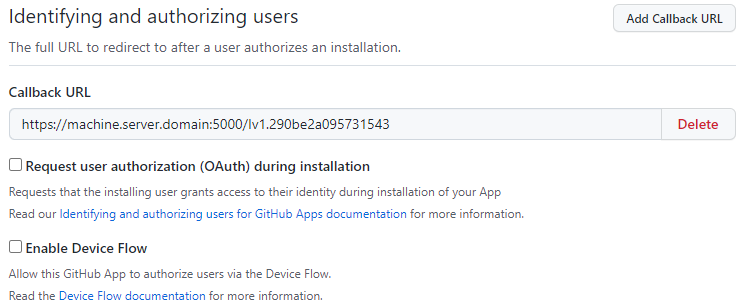
Press Save Changes.
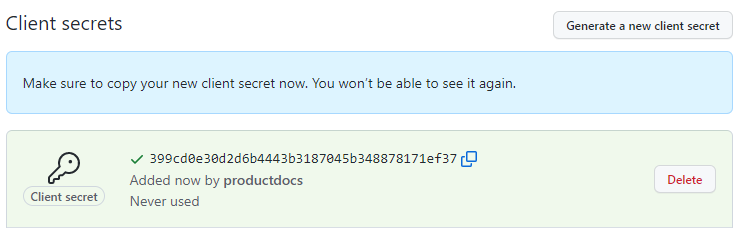
Press the Generate a new client secret button.
Copy the client secret.
Load ATS Security and open the Identity providers blade.
Click Add.
Select Github in the Type dropdown box.
Enter a Name for the identity provider i.e. GitHub.
Enter the App ID in the the Client Id field.
Enter the client secret in the Client secret field.
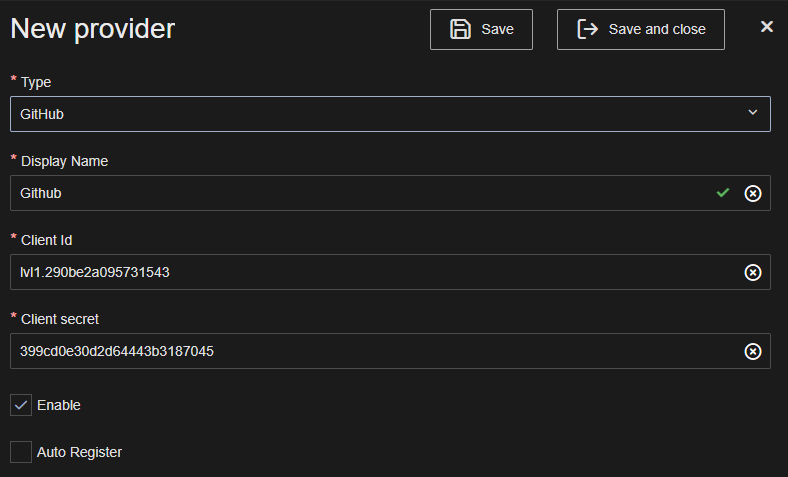
Press Save or Save and close.
The following message will be displayed:
Adding new identity provider of type GitHub. This change will take effect after application restart.
Log out of ATS Security.
Go back to ATS Security and the GitHub logo will be present on the right.
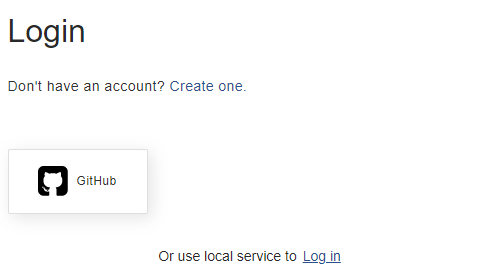
Press the GitHub logo. The GitHub login form is displayed.
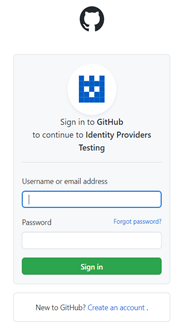
Enter the GitHub credentials and click Sign in.
If the user is already logged in in the GitHub app, another form will be presented prompting the user to authorise the app. Click on Authorize <App name>.
After logging in, the user should be successfully redirected and logged into ATS Security and Configuration Manager.
Google Identity Provider
Before proceeding with configuring Google as an Identity Provider, the user must have a Google account.
Go to https://console.cloud.google.com/
Log in with your gmail account.
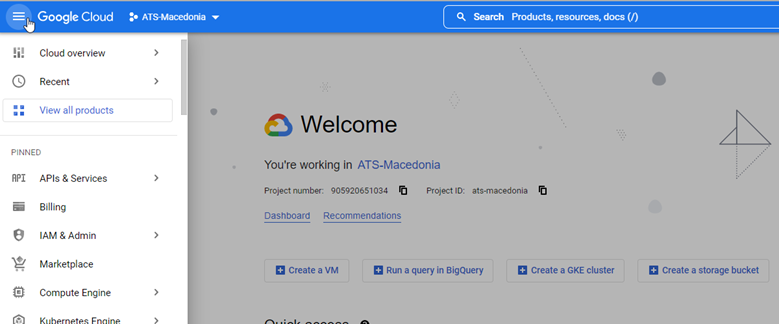
Click on the Google Cloud menu and choose API & Services followed by Credentials.
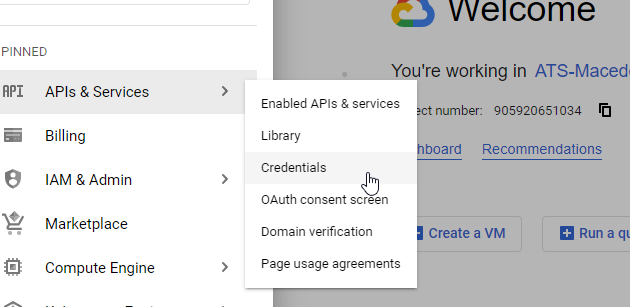
Click on the + Create credentials button and click on OAuth client ID.
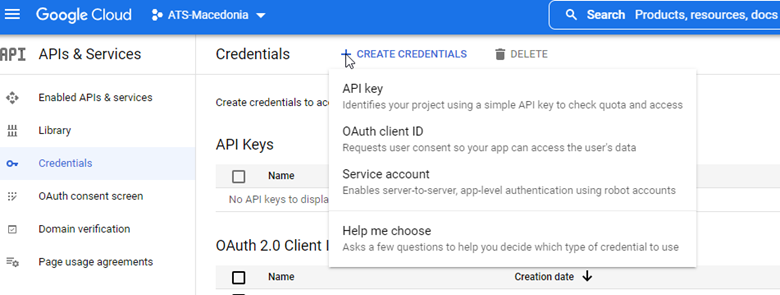
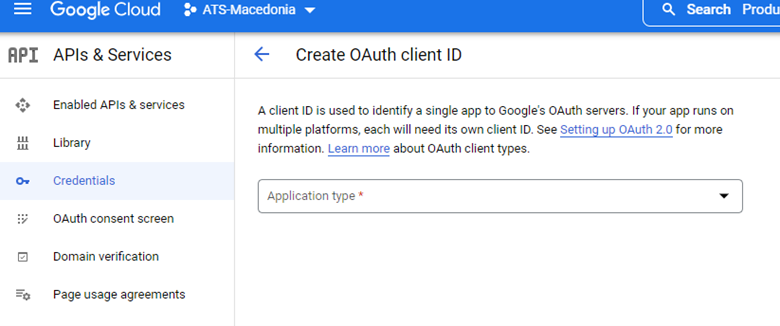
From the Application type drop-down choose Web application.
Enter a name for the application.
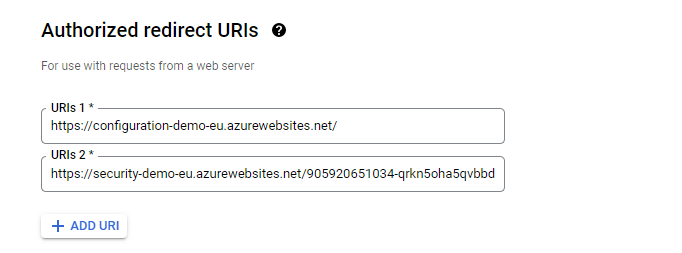
In the Authorized redirect URIs section click on the Add URI button and enter the URI value for the application.
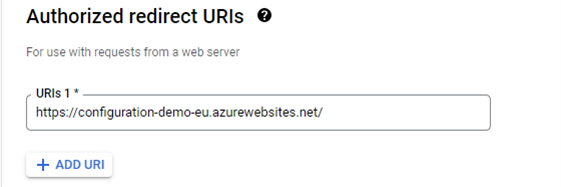
Click Create.
A window will pop-up saying that OAuth client is created. The user can see the Client ID and Client Secret.
Copy the Client ID and click OK.
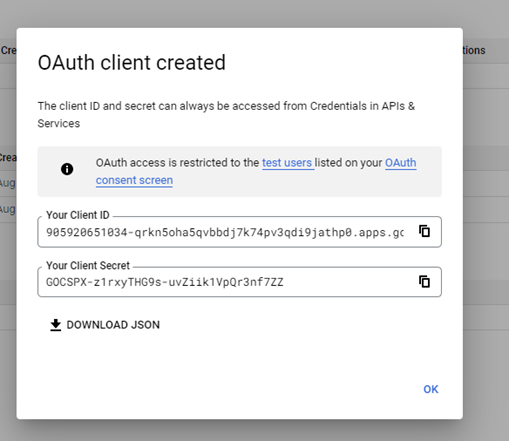
Click on the recently created application and in the Authorized redirect URIs click on Add URI.
Enter the application URI and paste the Client ID.
Click on the Reset Secret button. A new Client secret is generated.
Copy the client secret.
Click Save.
Load ATS Security and open the Identity providers blade.
Click Add.
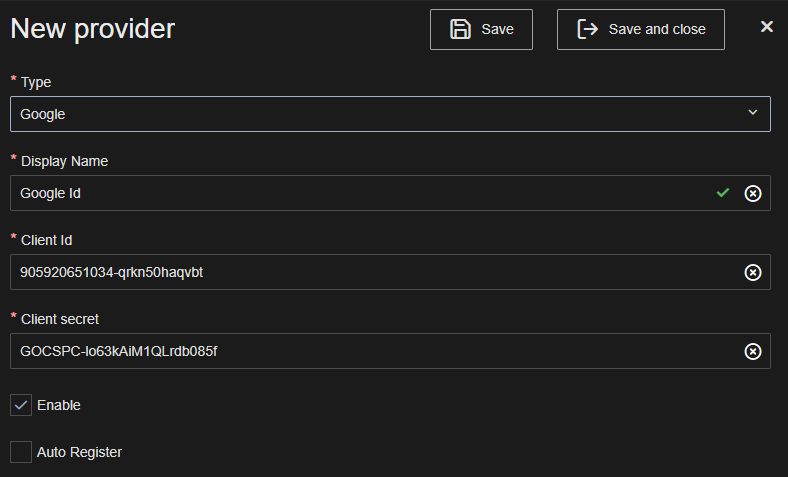
Select Google in the Type dropdown box.
Enter a Name for the identity provider i.e. Google.
Enter the App ID in the the Client Id field.
Enter the client secret in the Client secret field.
Press Save or Save and close.
The following message will be displayed:
Adding new identity provider of type Google. This change will take effect after application restart.
Log out of ATS Security.
Go back to ATS Security and the Google logo will be present on the right.
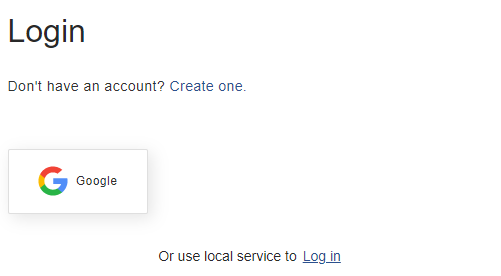
Press the Google logo. The Google login page is displayed.
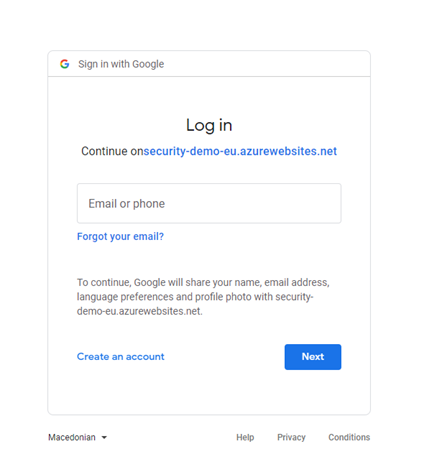
Enter the Google credentials and click Next.
After logging in, the user should be successfully redirected and logged into ATS Security and Configuration Manager.
SAML Identity Provider
Create SAML application in Okta
To use the SAML identity provider in ATS Security Manager first a SAML application is required to be created. For the purpose of this example, Okta will be used.
First go to https://developer.okta.com/ and sign up. The Okta account can be used to and register applications later.
Check the provided link for how to create a SAML application in Okta :
https://help.okta.com/en/prod/Content/Topics/Access-Gateway/add-app-saml-pass-thru-add-okta.htm
Signed in to Okta as admin.
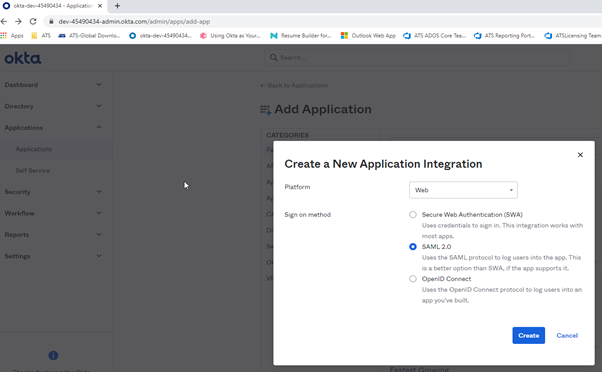
Create a Saml application
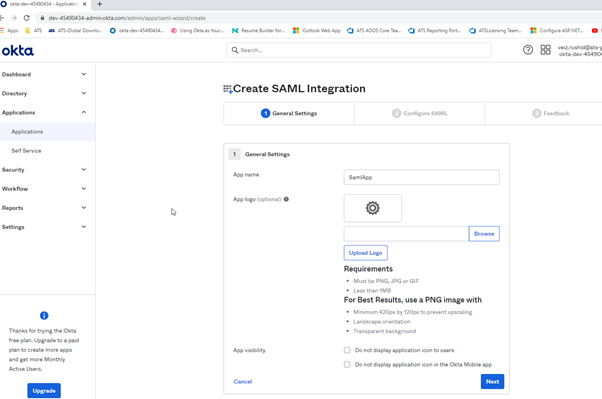
After clicking Create button you should insert first the general settings for the application.
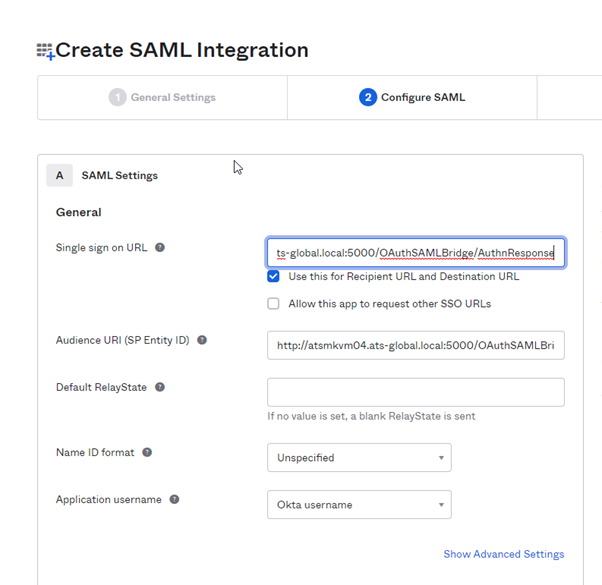
Once the general settings have been completed, the single sign on URL needs to be specified. The URL should be similar to the below example.
https://securitymanagerurl/OAuthSAMLBridge/AuthnResponse where https://securitymanagerurl/ is your ATS Security Manager application
This is the endpoint of the security manager application that handles the saml responses.
After the Configure SAML section specify that this is the internal app and click Finish.
After successful configuration of the SAML application, view the setup Instructions of the application.
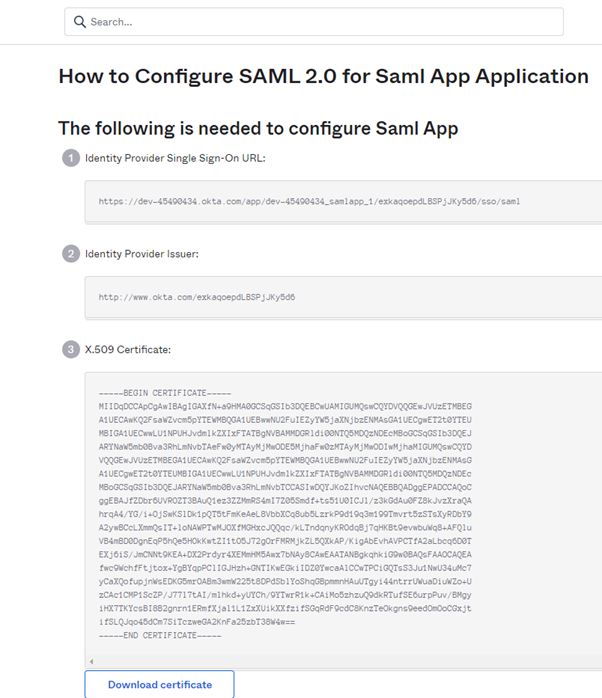
These two properties Identity Provider Single Sign-On URL and Identity Provider Issuer can be used later on in ATS Configuration Manager for configuring of Saml Identity provider.
How to configure SAML Identity Provider in ATS Configuration Manager
To configure identity providers in ATS Security Manager ,navigate to the Security card and go to the Identity Providers section on the menu to the left. Use the SAML application details from the View Setup Instructions in Okta to configure the SAML identity provider.
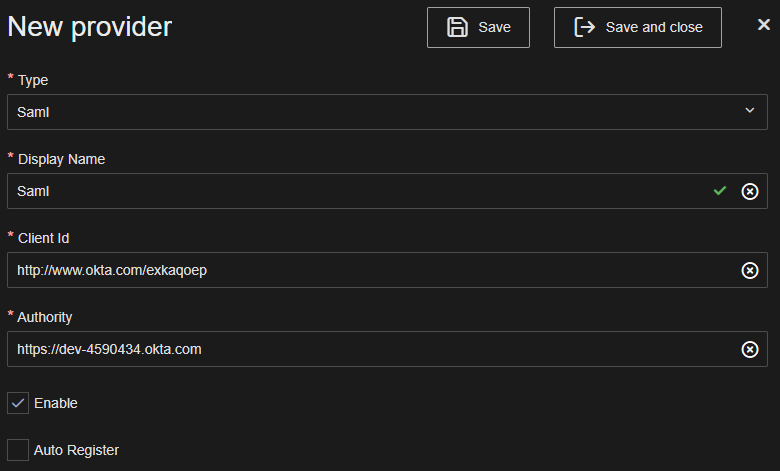
The following properties should in Security Manager should be mapped accordingly with the properties in the Okta configuration described in the previous chapter:
ClientId = Identity Provider Issuer
Authority = Identity Provider Single Sign-On URL
Assignments in SAML application in Okta
Following the successful configuration of the SAML application in Okta, users and groups can be assigned to the application in the Assignments section. The application can be only be used to assigned users or groups.
Expected Result
It is most important when configuring the SAML application that the single endpoint is assigned so SAML responses will be sent.
For example: http://securitymanagerurl/OAuthSAMLBridge/AuthnResponse where http://securitymanagerurl is your ATS Security Manager service.
The configured SAML application can be used only by one ATS Security Manager.
If there are multiple instances of ATS Security Manager service deployed on different machines, then a SAML application is required for each instance.