The installer for ATS Security and Configuration manager installs ATS Configuration manager and includes the ATS Security configuration plug-in as well as the ATS Start application.
Installation of ATS Security and Configuration manager
This section describes the installation process. Should a previous version of ATS Security and Configuration Manager exist, it must be uninstalled before proceeding.
Before you start the installation for ATS Security and Configuration manager make sure you have access to MSSQL Server instance that has enabled Windows and SQL Authentication.
Download and unpack the setup for ATS Security and Configuration manager.
Run the ATS.SecurityConfigurationManagerWs.1.8.x.x.exe.
The installer for ATS Security and Configuration manager is published as a self contained executable. This mean that the application contains all the components of the application, including the .NET libraries and target runtime. The application is isolated from other .NET applications and does not use any locally installed shared runtimes.
The prerequisites screen will appear only if Microsoft Visual C++ Redistributable Packages and SQL Server ODBC driver are missing.
At the welcome screen click Next.
Accept the license agreement and press Next.
Browse to a different installation location if required. Press Next.
Specify an MSSQL server name or server instance name along with a user that has permission to create databases. Finally, provide a name for the database. Press Next.
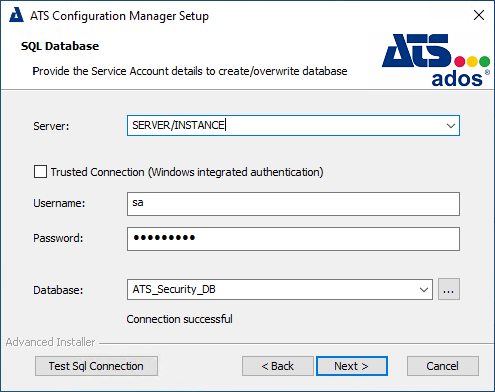
The details specified will be used to create a database for ATS Security, which will hold details of users, their roles and the applications they can access.
If the database specified above already exists it will be overwritten, otherwise a new database will be created.
Enter a username and password to be used for the ATS Security database. If the credentials specified do not currently exist, they will be created by using the credentials from the previous step and assigned as Scheme Owner. If the database is an Azure SQL Server, the database user specified in this step must be previously created and configured with the db_owner role. Press Next.
Enter the following configuration details:
SSL Certificate (HTTPS only): Specify the SSL Certificate.
For information on creating a certificate, please click here.
Server Name: Enter the name of the machine that hosts the ATS Security and Configuration Manager.
Port (Security Manager): Enter the port number to be used for the Security Manager. The default is 5000.
Port (Start): Enter the port number to be used for ATS Start. The default is 4400.
Port (Configuration Manager): Enter the port number to be used for the Configuration Manager. The default is 4200.
Press Next.
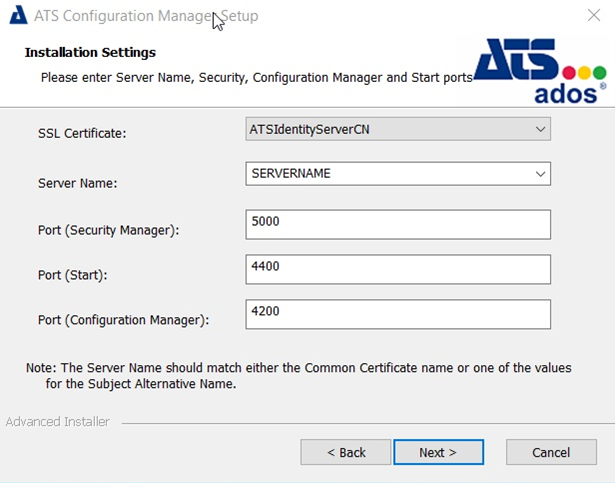
The server name specified must match with the certificates' CN value.
ATS Security, ATS Start and ATS Configuration Manager are browser based HTML5 applications and use OAuth2 authentication. Browser based applications should always use HTTPS but it is mandatory for OAuth2. Most companies that operate an Active Directory also operate an integrated CA (Certificate Authority). All domain computers will trust a certificate issued by that CA.
For further information on configuring ATS Security, ATS Start and Configuration Manager for HTTPS, please click the link.
If the application is published via a reversed proxy, then go to step 10, otherwise proceed to step 11.
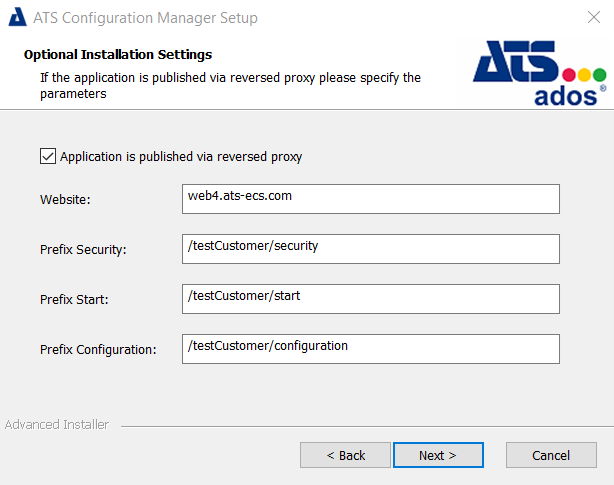
Place a tick in the Application is published via reversed proxy checkbox and enter the following fields:
Website: Define the domain from your reverse proxy. The website should not end with slash ( / ).
Prefix Security: Define the prefix for Security Manager. Prefix Security should begin with a slash ( / ).
Prefix Start: Define the prefix for Start. Prefix Start should begin with a slash ( / ).
Prefix Configuration: Define the prefix for Configuration Manager. Prefix Configuration should begin with a slash ( / ).
Click Next.
Click Install.
Once the installation is complete, press Finish.
If the Launch ATS Start check box was ticked in the previous step, a browser window displaying the ATS Security login page will be loaded.
Two built-in users are included with the installation: Admin and Guest. The passwords for these users are Admin2018! and Guest2018! respectively. Upon first login with either of these users you will be redirected to the change password page to set new password for the user.
Upgrade ATS Configuration Manager and Security Manager
The process for upgrading ATS Configuration Manager and Security Manager is determined by the current version installed.
If upgrading from version 1.4, the user is prompted to confirm that they would like to proceed with the upgrade. If Yes is selected, the software is upgraded automatically to the latest version. This process retains all previous configuration and registration information.
Versions older than 1.4 are required to be removed before the latest version is installed. Attempts to upgrade will present the user with an error message and the installation is aborted. Users should manually remove the current version and perform a fresh installation of the latest release. Please note that the previous configuration will be lost and the applications will require re-registering.
When upgrading from versions equal to or older than 1.7, the user is prompted to confirm they would like to proceed with the upgrade. If Yes is selected, a new screen will open asking for the port number of the ATS Start application.

After specifying the port the installer will proceed with the upgraded installation.
Unattended installation
The installation package for ATS Security and Configuration Manager can be run as an unattended installation.
An unattended installation or silent/quiet install is where the installation of a software program can be completed without any user interaction. The installer runs from start to finish without interrupting the user.
To achieve this, several parameters are required when executing the installation using the command prompt. The example below indicates the values to be replaced in bold.
<NAME-OF-INSTALLATION-PACKAGE>.exe /exenoui /qn /L*V "C:\silent\InstallConfSecLog.txt" SERVER_PROP="(local)\SQLEXPRESS" USERNAME_PROP="test123" PASSWORD_PROP="test123" DATABASE_PROP="security_210922_01" EDIT_NEW_DLG_LOGIN_ID_PROP="test123" EDIT_NEW_DLG_PASS_PROP="test123" CBTYPE_1_PROP="https" HTTP_S="https" EDIT_NEW_DLG_HOST_NAME_PROP="ATSMKNB012.ats-global.local" EDIT_SEC_MEN_PORT_PROP="5000" EDIT_CONF_MNG_PORT_PROP="4200" CBSSL_PROP="ATSMKNB012.ats-global.local" SSL_CN="ATSMKNB012.ats-global.local" GO_INSTALL="TRUE" SILENT_INSTALL="TRUE" EDIT_START_PORT_PROP="4400"
The Parameters that are provided for quiet installations are:
SERVER_PROP: The name of the server where the database will be created.
USERNAME_PROP: The user that has rights to create a database. Used in conjunction with SQL_TRUSTED_CONNECTION.
SQL_TRUSTED_CONNECTION: Specifies the authentication method to use. If the property is set to "1" then Trused SQL Authentication is selected and it will use the windows account under which the installer is started. If "" is set then it will use SQL Authentication. The default value is 1.
EDIT_NEW_DLG_LOGIN_ID_PROP: The username for SQL user that will be used to connect to the database. This user requires access to the database only. Admin rights to the server and database are not required.
EDIT_NEW_DLG_PASS_PROP: The password for the user that is used to connect to the database.
CBTYPE_1_PROP: Indicate which protocol will be used. I.e. HTTP or HTTPS
HTTP_S: Used in scripts where configuration URLs are built and must have the same value as CBTYPE_1_PROP. I.e. HTTP or HTTPS.
EDIT_NEW_DLG_HOST_NAME_PROP: The name of the host where the software is installed.
EDIT_SEC_MEN_PORT_PROP: The ort value for Security Manager. Default is 5000.
EDIT_CONF_MNG_PORT_PROP: The port value for Configuration Manager. Default is 4200.
CBSSL_PRO: The name of the certificate that will be used if the software is installed for HTTPS.
GO_INSTALL: Used during the upgrade of the software and indicates that the user accepts the upgrade.
SILENT_INSTALL: The default value is FALSE and indicates to the installer if some scripts need to be executed if installation is run in silent mode.
SSL_CN: The Certificate Common Name Value
EDIT_START_PORT_PROP: The port number for ATS Start. The default is 4400.
Error Log
It is recommended to enable logging so that any issues that may occur during an unattended installation can be identified. Ensure the location of the text file, indicated in bold in the below example, is valid.
<NAME-OF-INSTALLATION-PACKAGE>.exe /exenoui /qn /L*V "C:\silent\InstallConfSecLog.txt"
An example error log
<NAME-OF-INSTALLATION-PACKAGE>.exe /exenoui /qn /L*V "C:\silent\InstallConfSecLog.txt" SERVER_PROP="(local)\SQLEXPRESS" USERNAME_PROP="test123" PASSWORD_PROP="test123" DATABASE_PROP="security_210922_01" EDIT_NEW_DLG_LOGIN_ID_PROP="test123" EDIT_NEW_DLG_PASS_PROP="test123" CBTYPE_1_PROP="https" HTTP_S="https" EDIT_NEW_DLG_HOST_NAME_PROP="ATSMKNB012.ats-global.local" EDIT_SEC_MEN_PORT_PROP="5000" EDIT_CONF_MNG_PORT_PROP="4200" CBSSL_PROP="ATSMKNB012.ats-global.local" GO_INSTALL="TRUE" SILENT_INSTALL="TRUE" EDIT_START_PORT_PROP="4400"
If an older version of the software is detected the installation will be aborted. The log will feature a message stating that another version has been found.
SameSite cookies browser changes
The Chrome (<90) and all newer browser version are changing the default behavior for how cookies will be sent in first- and third-party contexts to avoid cross-site forgery attacks, malicious tracking and data leakage.
The new update is using SameSite cookie attribute which tells browsers how cookies should be handled (allow or block cookies depending on attribute).
In the newer browser version SameSite attribute will be turned on by default, and this mean by default cookies are restricted to first party access and need explicitly cookies to be marked for access in third-party context.
All cookies without SimeSite attribute will be restricted to first party access only, if we want cookie to be used in third-party context they must be marked as SameSite=None and Secure and this also mean that third-party cookies will be sent only over HTTPS connection.
To be compliant with this new default browser behavior ATS Security Manager apply these changes to issued cookies:
When site is configured on HTTPS issued cookies are marked as SameSite=None and Secure
When site is configured on HTTP issued cookies are marked as SameSite=Strict (also knowing that this will affect refreshing of token, when HTTP configuration is used auto refreshing of token is disable. When token expires alert message is shown with information that token has expired and navigate user to the login screen).
If the application is being used from Microsoft Edge or Chrome and the application is not set under https, users may experience issues like:
after changing the password in the form of "An error occurred during the login process. Please try again".
or
after entering valid credentials in the form, the user is authenticated but redirected again to the login page
This is mostly because of the security settings enforced by the browser. There are 2 possible solutions
Configure the application to run under https
Configure the browser and disable Same Site properties (For more details see 'How to configure Chrome' or 'How to Configure Edge')
How to configure Chrome
Open Chrome and open a new tab and enter chrome://flags
In the search box type "samesite" and you will be displayed with the following options
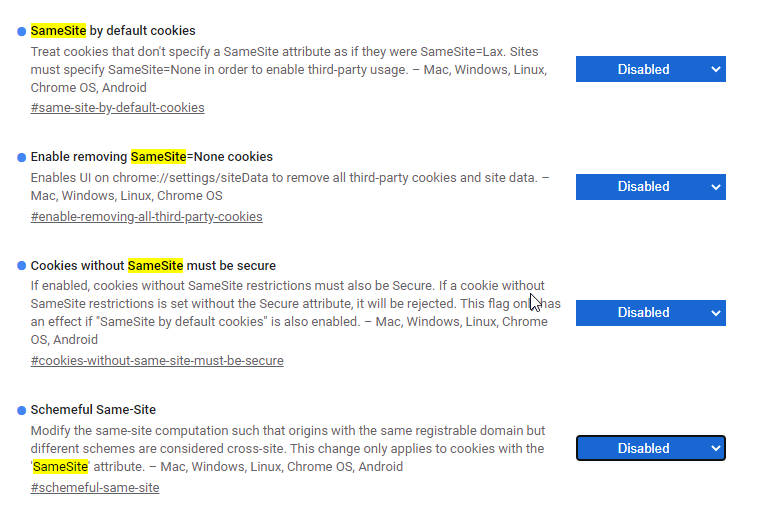
Set all those properties as disabled and relaunch Chrome
How to Configure Edge
Open Edge and open a new tab and enter edge://flags
In the search box type "samesite" and you will be displayed with the following options
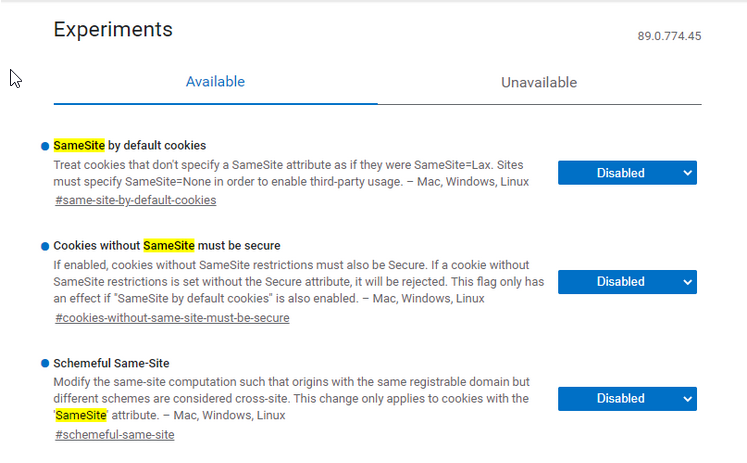
3. Set all those properties as disabled and relaunch the browser
Configure Cross-Origin Requests (CORS)
Configuring CORS policies allows ATS Configuration Manager to be accessed on other domains.
For further information, please click here.